
Key Highlights
- Comprehensive SIP Security – How an SBC shields Asterisk servers from threats like registration hijacking, DoS/DDoS, call fraud, and eavesdropping.
- Beyond Protection – Additional benefits include call routing optimization, protocol interworking, and regulatory compliance support.
- Actionable Best Practices – Practical steps to choose, deploy, and maintain an SBC for maximum Asterisk SIP security and performance.
In the last few years, SIP-based cyberattacks have skyrocketed, targeting VoIP infrastructures worldwide. Open-source telephony platforms like Asterisk have been particularly tempting for attackers.
Why?
While Asterisk offers unmatched smart scalability features and traffic management techniques, it also operates in an environment where SIP protocol vulnerabilities can be exploited by those looking to disrupt services, steal data, or commit fraud.
The truth is, even the most well-configured Asterisk server isn’t invincible. Hackers know exactly how to probe for weak points, from unprotected SIP ports to poorly authenticated endpoints, and once they gain access, the consequences can be costly. this is where the Session Border Controller (SBC) steps in. Think of it as both a security guard and a traffic manager for your VoIP network. The right Asterisk SBC server can filter out malicious SIP traffic, safeguard communications, and optimize performance, all before suspicious packets even reach your system.
In this blog, we’ll break down five critical ways an SBC protects your Asterisk server from SIP vulnerabilities while keeping your calls secure, clear, and uninterrupted.
But first, let’s set the foundation.
What is SIP?
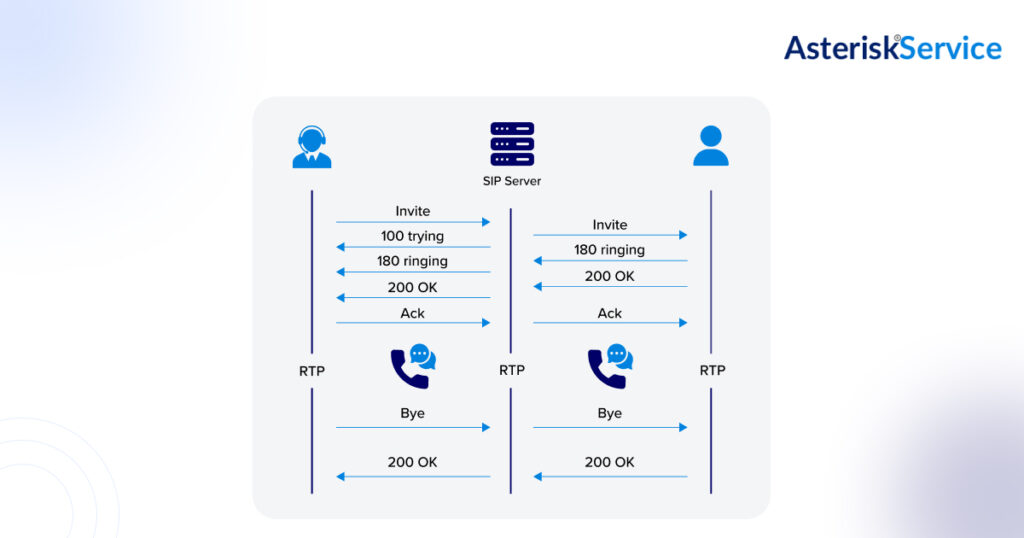
SIP, or Session Initiation Protocol, is the signaling protocol that enables voice and video calls over the Internet. It’s what tells devices how to set up, manage, and end communication sessions. If VoIP were a conversation, SIP would be the language people use to start talking, keep the discussion going, and know when to hang up.
The challenge?
SIP was designed for flexibility, not ironclad security. This makes it a prime target for attackers, leading to a range of SIP protocol vulnerabilities that can compromise both the network and sensitive call data.
Let’s take a closer look at the most common vulnerabilities that put Asterisk deployments at risk.
Common Threats to Asterisk Servers
An Asterisk server is a powerhouse for VoIP communications, but the moment it connects to the internet, it becomes part of a larger battlefield where SIP protocol vulnerabilities are actively exploited. Hackers don’t just randomly attack; they use automated scanning tools to specifically look for exposed VoIP systems, weak authentication, and outdated configurations. Let’s look at the major threats in detail:
1. SIP Registration Hijacking
This happens when an attacker gains access to valid SIP credentials, either by guessing passwords, stealing them through phishing, or capturing them over insecure connections. Once they have credentials, they can register their own device in place of yours, intercept calls, impersonate users, and even disrupt entire communication flows. For an unprotected system, this can happen in seconds.
2. Call Fraud / Toll Fraud
Call fraud is one of the most financially damaging SIP security vulnerabilities. Attackers exploit weaknesses in authentication or access controls to place unauthorized calls, often to premium-rate numbers they control. A single weekend of such fraudulent activity can result in thousands of dollars in charges.
3. Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS)
Attackers can flood your Asterisk server with SIP requests, especially SIP INVITEs, at a rate the system can’t handle. A targeted DDoS attack can completely halt legitimate calls, leading to frustrated customers and business downtime.
4. SIP Fuzzing and Malformed Packet Attacks
SIP fuzzing involves sending deliberately corrupted or malformed SIP packets to the Asterisk server, trying to trigger bugs or crashes. This type of attack can cause instability, memory leaks, or even expose deeper security flaws.
5. Eavesdropping & Man-in-the-Middle Attacks (MITM)
Without encryption, SIP signaling and RTP media streams can be intercepted, allowing attackers to listen in on calls or alter call content in real-time. This not only compromises privacy but can also lead to serious compliance violations.
Why Traditional Firewalls Aren’t Enough?
While a standard firewall can block some suspicious IP addresses, it has no deep understanding of SIP. SIP signaling often involves dynamic port ranges, embedded IP addresses in packet payloads, and complex message flows that a traditional firewall can’t interpret. This leaves gaps that attackers exploit.
Asterisk telephony has come very far, and this is why modern security measures like SBC are essential. It understands SIP on a protocol level and can apply SIP protection strategies for Asterisk SBC that go far beyond what basic perimeter defenses offer.
So, What is an SBC?
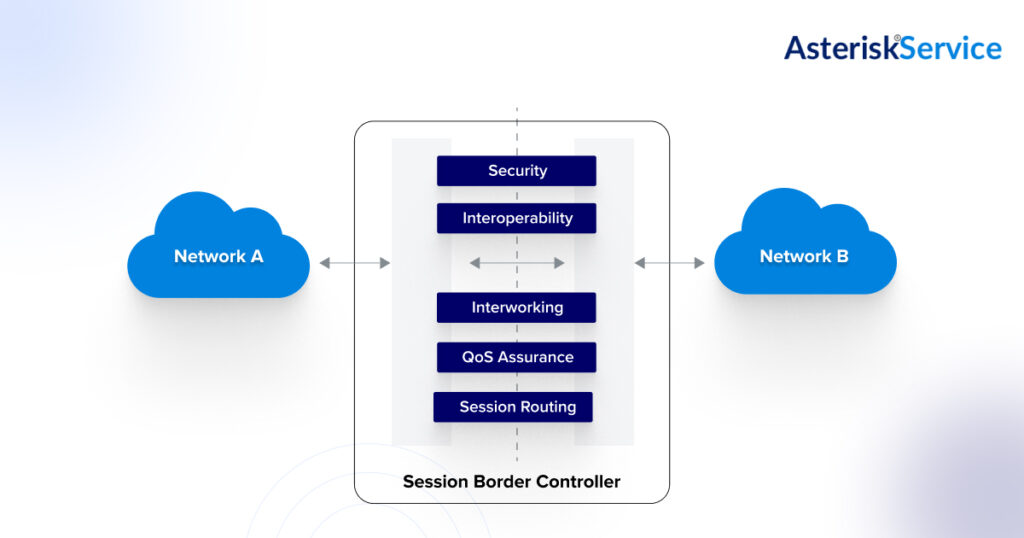
A Session Border Controller is a specialized network element that sits between your public SIP traffic and your Asterisk server. It inspects, filters, and manages all SIP communications, ensuring that only safe and authorized traffic gets through.
Unlike a standard firewall, an SBC understands VoIP protocols, can handle complex call routing, and adds extra session border controller security features for Asterisk.
Its dual role?
Security + Traffic Management, safeguarding against attacks while optimizing call quality. In most deployments, the SBC is placed right at the network edge, acting as a protective gateway between the open internet and your Asterisk system.
Let’s break down the five most effective SIP protection strategies for Asterisk SBC and see exactly how SBC protects SIP traffic in Asterisk from the moment a call request hits your network.
5 Ways SBC Protects SIP Traffic in Asterisk
Securing SIP traffic isn’t just about blocking threats; it’s about managing and safeguarding every call before it reaches your Asterisk server. An SBC acts as both a shield and a smart traffic controller to keep your VoIP safe.
Let’s explore each of its protective features in detail:
1. SIP Traffic Filtering & Deep Packet Inspection
Unlike a generic firewall, an SBC examines SIP headers, call setup messages, and even media negotiation details. It can identify malformed packets, block unauthorized SIP methods, and drop suspicious calls before they reach the Asterisk core. This prevents SIP fuzzing and malicious injection attempts that exploit SIP protocol vulnerabilities. Deep packet inspection also ensures that legitimate calls aren’t accidentally blocked, keeping service disruption to a minimum.
2. DoS & DDoS Attack Mitigation
The SBC can detect abnormal traffic patterns, like sudden spikes in SIP INVITE requests, and apply intelligent rate limiting. It can block excessive attempts from specific IP addresses, filter out malformed floods, and even dynamically blacklist sources. This means even under heavy DDoS pressure, your Asterisk SBC continues to pass legitimate traffic without overwhelming the server.
While SBCs handle the security side of things, pairing them with innovations like Asterisk and AI integration can unlock smarter call handling, predictive analytics, and enhanced customer experiences alongside robust protection.
3. Secure Remote Access & Topology Hiding
Remote workers often need to register phones from outside the office. An SBC allows this securely by using TLS tunnels, VPN-like connections, or secured SIP trunks. It also hides your internal network structure by replacing private IPs with the SBC’s own, preventing reconnaissance scans from mapping your infrastructure, a crucial session border controller security feature for Asterisk
4. SIP Authentication & Access Control
SBCs enforce strict authentication policies, ensuring only trusted devices can connect. This includes enforcing strong passwords, client certificates, or IP whitelisting. They can also blacklist suspicious endpoints dynamically, protecting against brute-force SIP registration attacks. This layered access control is a core part of best SBC practices for Asterisk SIP security.
5. Encryption & Media Security
An SBC supports TLS for SIP signaling and SRTP for media streams, ensuring conversations are unreadable to outsiders. This protects against eavesdropping, replay attacks, and MITM exploits. Encryption also helps you comply with industry regulations like HIPAA or PCI-DSS, where secure transmission is mandatory.
Enhancing security is only one aspect; managing and reducing VoIP communication costs with Asterisk and SIP trunking is equally important.
By combining deep protocol awareness with intelligent security enforcement, an SBC acts as a purpose-built shield for your Asterisk environment. It doesn’t just block threats, it actively shapes and manages SIP traffic so your communications remain secure, stable, and high-performing, even in the face of persistent attacks.
While security is often the first reason businesses deploy an SBC, its advantages extend far beyond threat prevention. In fact, integrating an SBC with your Asterisk system can unlock new levels of call quality, interoperability, and compliance, all of which contribute to a more resilient and future-ready VoIP infrastructure.
Benefits of Using an SBC with Asterisk
While security is the main advantage, an SBC offers much more for your Asterisk deployment. From smarter call routing to compliance support, these added benefits can transform how your VoIP network performs.
Call Routing Optimization
The SBC can intelligently route calls based on least-cost routing (LCR), available bandwidth, or latency. This ensures calls take the best possible path, reducing delays and improving quality, all while taking load off the Asterisk server. SBC deployment with AI-powered solutions in Asterisk can unlock advanced call routing and real-time voice analysis
Protocol Interworking
In real-world deployments, not all devices or carriers speak the same “version” of SIP. An SBC can perform SIP normalization, or even translate between protocols, such as SIP to SIP-I or SIP to WebRTC. This compatibility layer ensures your Asterisk SBC server can communicate seamlessly with different vendors, carriers, and endpoints.
Regulatory Compliance
Meeting standards like PCI-DSS, HIPAA, or GDPR isn’t just about encryption, it’s also about audit logging, call recording controls, and secure signaling. An SBC’s advanced logging and policy enforcement make compliance far easier, reducing risk during audits.
When you combine these advantages with the advanced session border controller security features for Asterisk, you’re not just protecting your VoIP system; you’re also unlocking higher performance, smoother interoperability, and long-term compliance. An SBC isn’t a “nice-to-have” for Asterisk; it’s an essential component for any business that values secure, reliable, and future-ready communications.
Of course, simply having an SBC for security in place isn’t enough; how you deploy, configure, and maintain it will determine the real-world effectiveness of your Asterisk SBC server. Following proven best practices ensures your investment delivers maximum security, optimal performance, and resilience against evolving SIP protocol vulnerabilities. Let’s explore the key steps to get it right from day one.
Best Practices for Integrating an SBC with Asterisk
Deploying an SBC is only half the battle; using it effectively is where the real value lies. These proven practices will help you get the most from your SBC while maximizing Asterisk SIP security.
Choosing the Right SBC
Decide whether a hardware, virtual, or cloud-based SBC is best for your needs. High-traffic enterprises may need a robust hardware model, while smaller deployments can leverage virtual or hosted SBCs for flexibility.
Correct Network Placement and Configuration
The SBC should sit at the network edge, between the public internet and your Asterisk server. This ensures all SIP traffic passes through it for inspection and policy enforcement. Proper NAT traversal settings, firewall integration, and SIP trunk configuration are essential here.
Regular Firmware and Security Updates
Cyber threats evolve constantly. Keeping your SBC’s firmware and security definitions updated ensures it can defend against the latest exploits targeting SIP protocol vulnerabilities.
Monitoring Logs and Alerts
An SBC generates valuable insights, from traffic volumes to failed registration attempts. Monitoring these logs allows proactive responses to unusual patterns, preventing incidents before they escalate. Pairing automated alerts with human oversight gives you the best balance between speed and accuracy.
Following these best SBC practices for Asterisk SIP security ensures your system remains not only safe but also optimized for consistent, high-quality communication.
With these insights into SIP vulnerabilities, SBC protections, and best practices in mind, let’s bring the discussion to a close and see why an SBC is indispensable for securing your Asterisk server.
Wrapping Up
SIP protocol vulnerabilities aren’t going away, if anything, they’re evolving. While Asterisk is a powerful and flexible telephony platform, it’s not immune to targeted VoIP attacks. Deploying an SBC adds a vital layer of session border controller security features for Asterisk, protecting against threats while optimizing call quality.
At Asterisk Service, we encourage every business to integrate an SBC as part of their SIP protection strategies for Asterisk SBC. The cost of prevention is always less than the cost of recovery, and with the right solution in place, your VoIP communications can remain secure, compliant, and high-performing for years to come.
FAQs
What is an SBC, and why is it important for Asterisk?
A Session Border Controller (SBC) is a security and traffic management device designed specifically for VoIP networks. Unlike traditional firewalls, an SBC understands SIP traffic, inspects call signaling, and blocks malicious activity before it reaches your Asterisk server. It’s essential for defending against SIP vulnerabilities like call fraud, DoS/DDoS attacks, and eavesdropping.
How does an SBC protect SIP traffic in Asterisk?
An SBC safeguards your VoIP system through SIP traffic filtering, deep packet inspection, DoS/DDoS mitigation, secure remote access, strict authentication, and encryption. These measures ensure that only safe, legitimate calls are processed by your Asterisk SBC server.
Can’t a firewall protect my Asterisk server from SIP attacks?
Standard firewalls provide basic network filtering but aren’t SIP-aware. They can’t interpret SIP headers, handle dynamic ports, or apply VoIP-specific security policies. This leaves gaps that attackers exploit, making an SBC a more effective choice for SIP security vulnerabilities.
What are the benefits of using an SBC beyond security?
In addition to security, an SBC offers call routing optimization, protocol interworking between SIP variants, and features to support regulatory compliance like PCI-DSS, HIPAA, and GDPR. These advantages improve performance, compatibility, and legal readiness.
How do I choose the right SBC for my Asterisk deployment?
Your choice depends on call volume, budget, scalability needs, and deployment model (hardware, virtual, or cloud-based). Look for SBCs with strong session border controller security features for Asterisk, easy integration, and vendor support.